Table of Contents
Background
Unexpected events are inevitable. There could be many things, internally or externally, that affect the progress and result of the project. To mitigate the impacts of these risks, it is important to conduct a risk analysis upfront. This risk assessment will cover risks comming from the project management and technical aspects. Risk events are evaluated based on their likelihood and severity, and hence are classified as acceptable, tolerable, undesirable and intolerable.
Risks Management
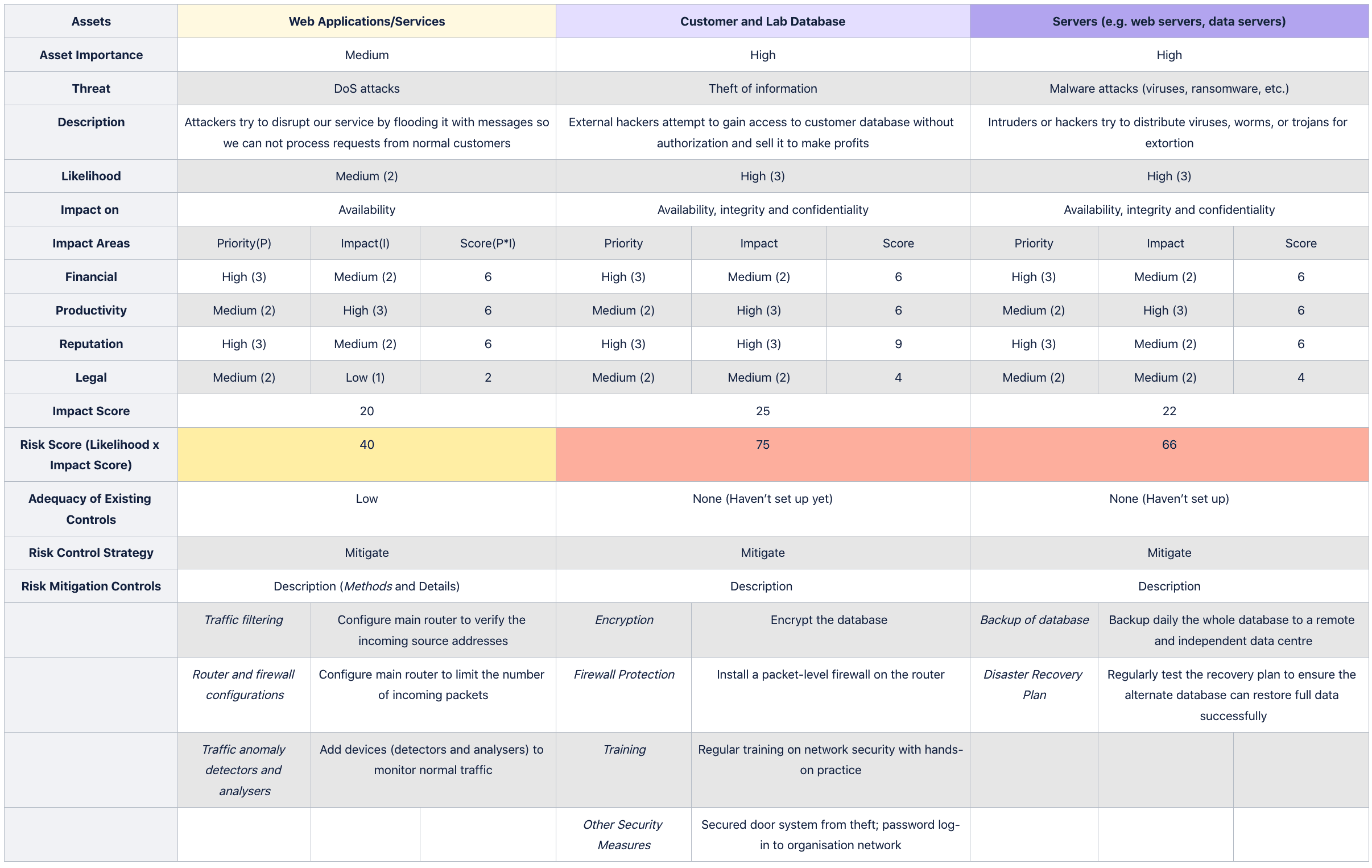
In accordance with the Risk Management Guide for Information Technology Systems(NIST guide) for the National Institution of Standards and Technology, we conduct five vital steps to assess the risks in our project:
- Develop risk measurement criteria
- Inventory IT assets
- Identify threats
- Document existing controls
- Identify improvements
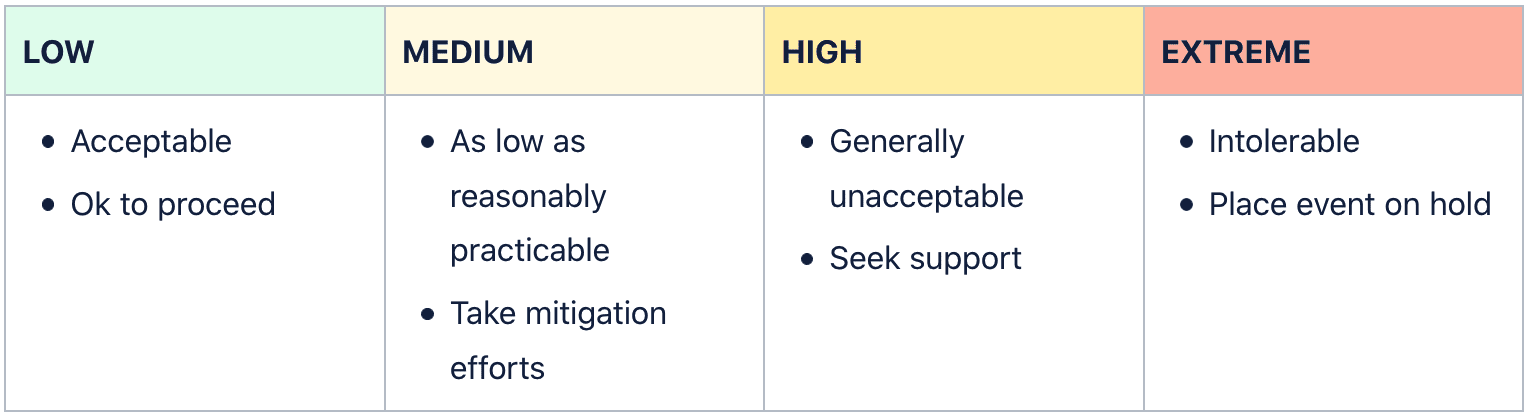
Risk Rating
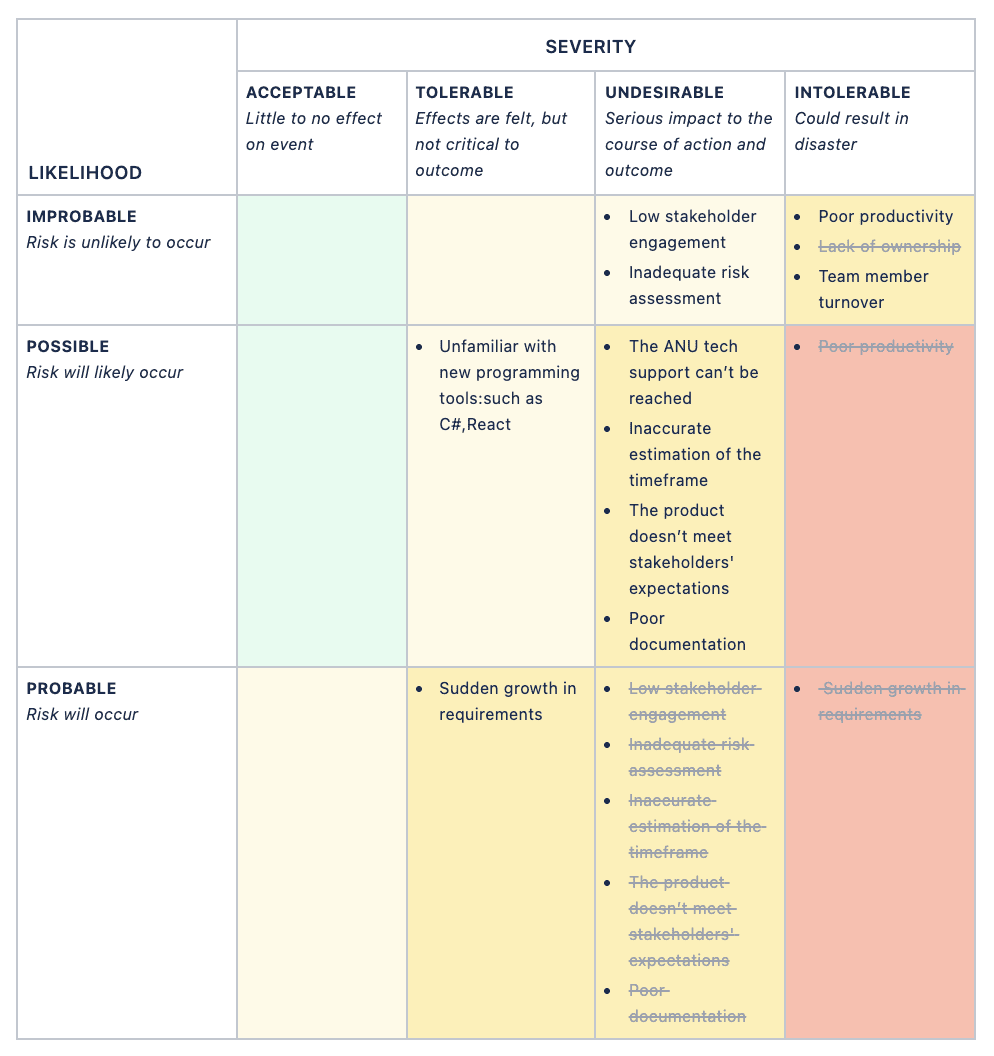
Project Management Risks
Attempted Approaches to mitigate risks:
- Poor productivity (Possible to improbable):
- Task tracking
- Change meeting routine: only the spokesperson meets with clients in this semester so that the developers can focus on development
- Lack of ownership (Improbable to impossible): signed the IP contract
- Low stakeholder engagement (Probable to improbable): active communication, set agendas before meetings so everyone can be more prepared, lucky to have nice stakeholders
- Inadequate risk assessment (Probable to improbable): research and open for advice
- The ANU tech support can’t be reached: drop-in, via email, via clients, in progress
- Inaccurate estimation of the timeframe (Probable to Possible): from communication to get to know the details of the project more
- The product doesn’t meet stakeholders’ expectations (Probable to Possible): agile methodology, integrating the prototype, and discuss with the clients many times.
- Poor documentation (Probable to Possible): team charter, work records, product requirements, statement of work, risk assessment, retrospectives…
- Sudden growth in requirements (Intolerable and Probable to Tolerable and Possible): using agile methodology, integrating the prototype, frequent and active communication with clients
- Team member turnover: maintaining a harmony communication environment
Future Approaches to mitigate risks:
- Poor productivity caused by unfamiliarity with the programming tools that are going to be used, such as C#, .NET, React: preferably use the technology stack that most team members use, otherwise more time will need to be scheduled to learn
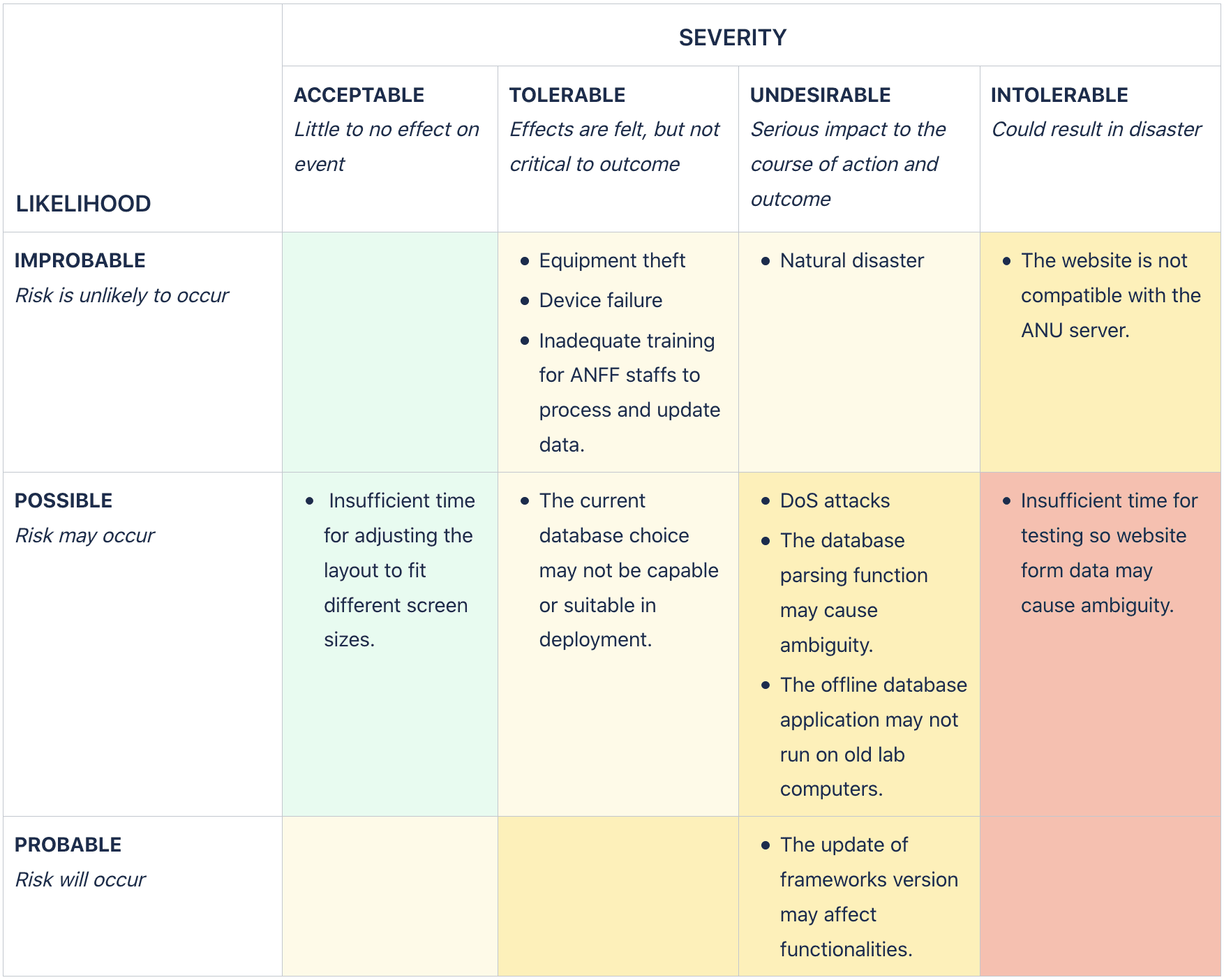
Technical Risks
Future approaches to mitigate risks:
-
The website is not compatible with the ANU server:
Communicate with the ANU IT department early before deployment. -
Insufficient time for testing so website form data may cause ambiguity:
Conduct regular testing throughout the development process.